Is the computer or mobile phone poisoned? Expert tips to help you stay away from viruses.
Cctv news: 2017 China Cyber Security Annual Conference closed in Qingdao on 24th. The recent popular ransomware has become the hot topic of the annual meeting.

2017 China Cyber Security Annual Meeting
According to incomplete statistics, the number of IP addresses infected with ransomware in China has exceeded 130,000, accounting for half of the infected IP in the world. At present, the spread of ransomware in China has been relatively effectively controlled.
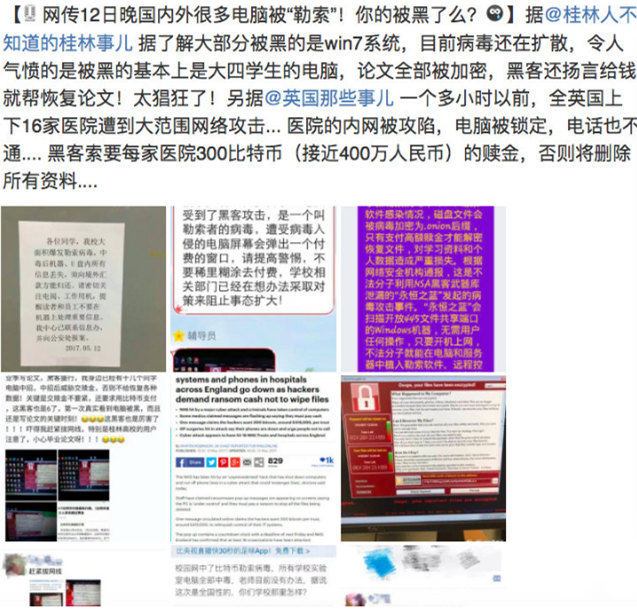
Source network
Intranet still has a high risk of being infected with ransomware.
Experts reminded that the current security alert of ransomware has not been completely lifted, and the risks mainly exist in the intranets of a large number of companies. It is suggested that intranet administrators should remain highly vigilant.
"Network Security" Big Data
This "blackmail virus" has caused more than 150 countries and regions around the world to "recruit", more than 300,000 computers have been blackmailed, and the ransom has reached 72,000 US dollars.
In recent years, network information security problems caused by viruses have been frequently exposed. According to the data of National Internet Emergency Center (CNCERT/CC), by the end of 2016, the total number of tampered websites in China had reached 62,894, and 9,756 information system security vulnerabilities had been collected, including 3,764 high-risk vulnerabilities, accounting for 38.6%. The number of mobile phone users in China has increased to 725 million, among which the total number of mobile phones infected with network viruses has reached 27.03 million. Network viruses have gradually become an important hidden danger affecting the information and property security of netizens in China.
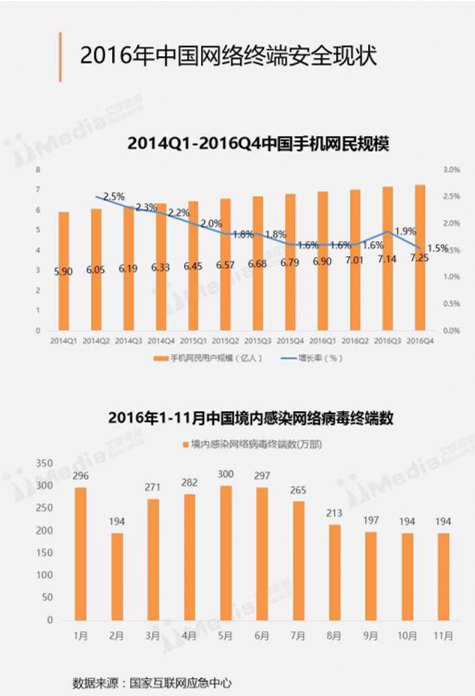
Data Map: Source Network
Problems existing in technical protection
1. The operating system is full of loopholes.
2. Too many access terminals are easy to break.
3. Protocol security is extremely fragile.
Expert advice:
First, the bank card is bound to the mobile phone, which is easy to be stolen. Without binding, you can avoid online fraud.
Binding the mobile phone number (at first) is as safe as setting the password and verification code. The safety effect cannot be completely achieved by one measure, but it may be more unsafe without protection. Just like locks at home, locking can’t prevent theft 100%, but not locking will have greater security risks.
Second, if the mobile phone receives a fraudulent call, it may be infected with a virus.
Infection with the virus leads to the deduction of fees and requires the implantation of virus files. There will be a process of installing virus program files when infected with virus. At present, there is no data communication on the phone, and the other party can’t implant virus through the phone.
Third, some QR codes contain viruses, and when they are scanned, they are poisoned.
Scan a QR code, first jump to a link. If it is a file, it will be poisoned after it is installed. If you scan it out, you won’t get caught without accessing or downloading the file.
4. The more complicated and secure the password setting for surfing the Internet?
This sentence is only half right. Because many user names and passwords are leaked now, hackers can crack the passwords according to the database collision. No matter how complicated it is, there is no way to ensure safety. What can we do? Different accounts, different user names and passwords.
(Note: Some texts and data source networks)